Microsoft Warns: Hackers Can Break Into Your Account – Even Without Your Password
Just when you think your business has locked down its cybersecurity, a new threat surfaces—and this one’s particularly sneaky.
Microsoft is raising the alarm about a rising cyberattack method that lets criminals access your accounts—without ever needing your password.
Yes, you read that right. No password required.
What Is Device Code Phishing?
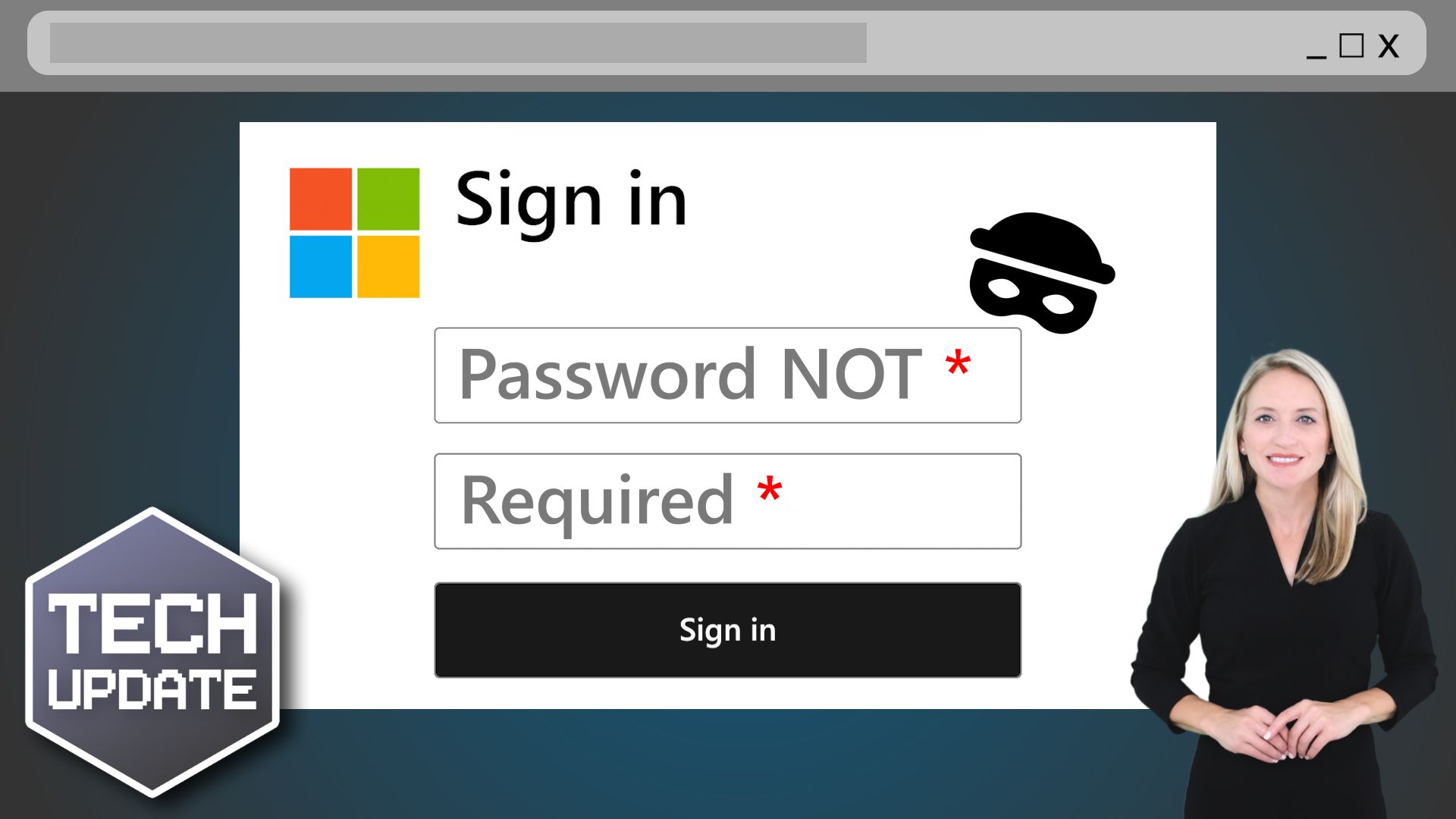
This latest tactic is called device code phishing, and it’s catching businesses off guard across the globe. Unlike traditional phishing scams that rely on tricking you into typing your password into a fake website, this method is much more subtle—and more dangerous.
Here’s how it works: Hackers send an email that looks completely legit. It might look like it’s from HR, a co-worker, or even a real Microsoft Teams invite. You click the link, and it takes you to an actual Microsoft login page.
Everything looks normal. No misspellings. No fake web addresses. Just the real deal.
You’re asked to enter a short code—called a device code. The email says it’s needed to confirm your login or join a meeting.
But here’s the twist: by entering that code, you’re unknowingly giving the attacker access to your Microsoft account on their device. It’s like unlocking the door to your office and handing them the keys—while thinking you’re just doing routine login steps.
Why This Threat Is So Dangerous
What makes device code phishing so scary is that:
-
It uses real Microsoft login pages, so everything appears trustworthy.
-
It can bypass multi-factor authentication (MFA)—even if you have extra protection in place.
-
You never give away your password, so it doesn’t trigger typical security alerts.
-
Hackers can stay logged in indefinitely by stealing your session token, which means changing your password won’t always kick them out.
Once inside, they can read your emails, access company files, impersonate you to colleagues, and more. The fallout can be huge—and it can all happen without any obvious warning signs.
How To Protect Your Business From Device Code Scams
1. Educate Your Team
The first line of defense is awareness. Teach your staff to pause and verify anytime they’re asked to enter a device code—especially if it’s unexpected or tied to a login request they didn’t initiate.
Remind them: Microsoft doesn’t send logins that require entering a code someone else provides. That’s a big red flag.
2. Verify Requests Through Other Channels
If something feels off, use a different method—like a phone call or your company’s secure chat—to check with the sender. Don’t rely solely on email.
3. Restrict Device Code Logins
If your business doesn’t need device code login for daily tasks, your IT team or provider can disable it entirely. This closes a major loophole and reduces your risk significantly.
4. Set Access Controls
Advanced security tools can block login attempts from unknown locations or devices. Limiting access to trusted environments makes it much harder for hackers to gain a foothold.
5. Ongoing Cybersecurity Training
Keep your team in the loop with regular cybersecurity refreshers. The more they know about the latest scams, the less likely they are to fall for them.
Stay One Step Ahead
Cyber threats are always evolving—but your protection strategies can too. With the right combination of awareness, tools, and policies, your business can stay secure even against clever tricks like device code phishing.
Need help tightening up your cybersecurity? We’re here to support your team with smart, simple solutions that make a real difference.
Next Steps
Are you looking for a new IT service provider? Check out our free guide that explains how to choose your next IT service provider for some quick tips to get you started! Schedule a free 15-minute discovery call with someone from our team to see if we’re a good mutual fit!